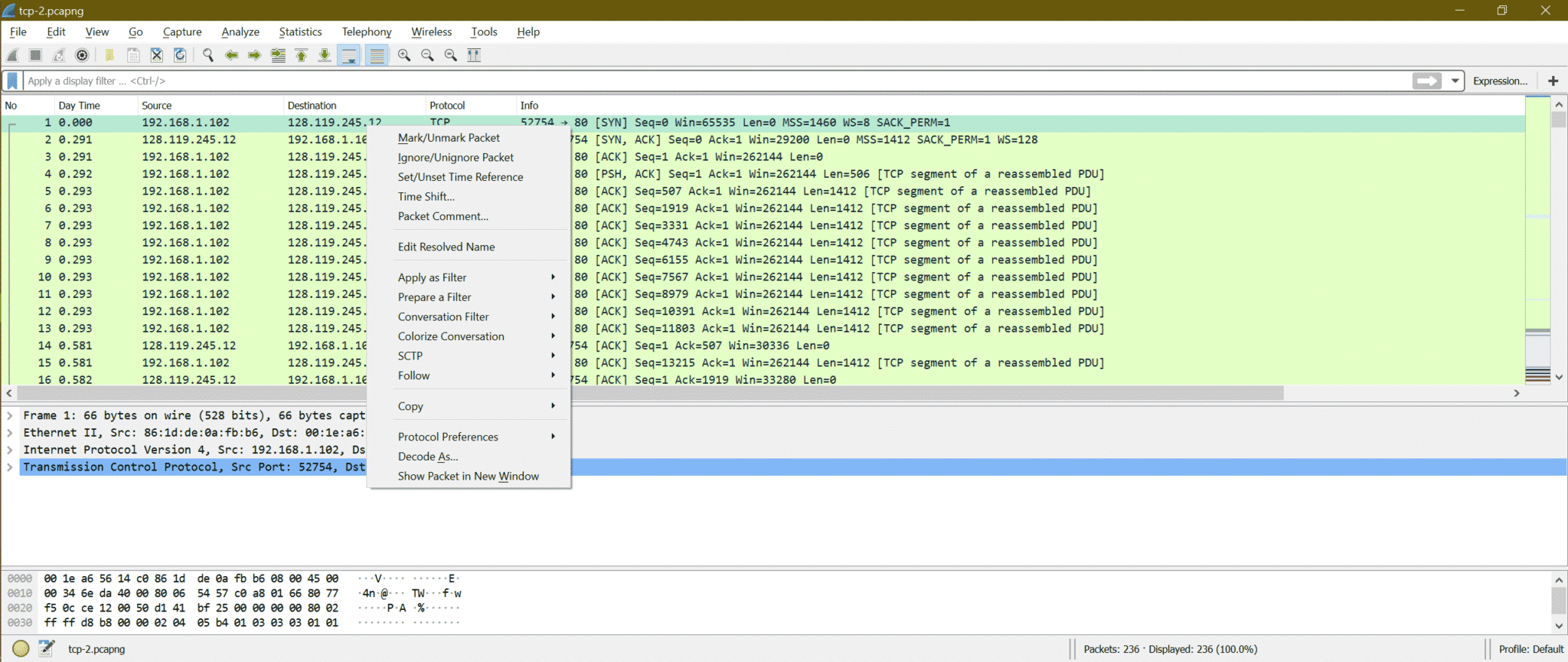
8 Wireshark Filters Every Wiretapper Uses to Spy on Web Conversations and Surfing Habits « Null Byte :: WonderHowTo
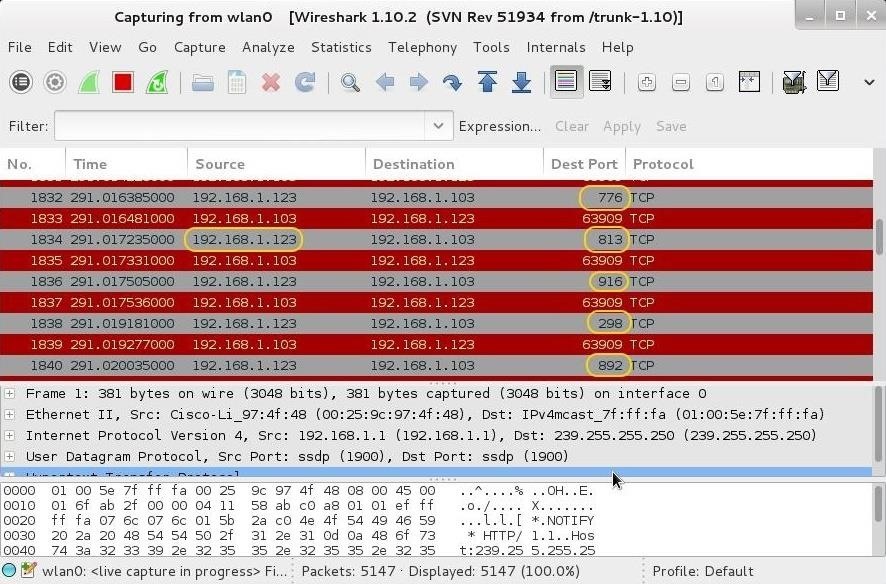
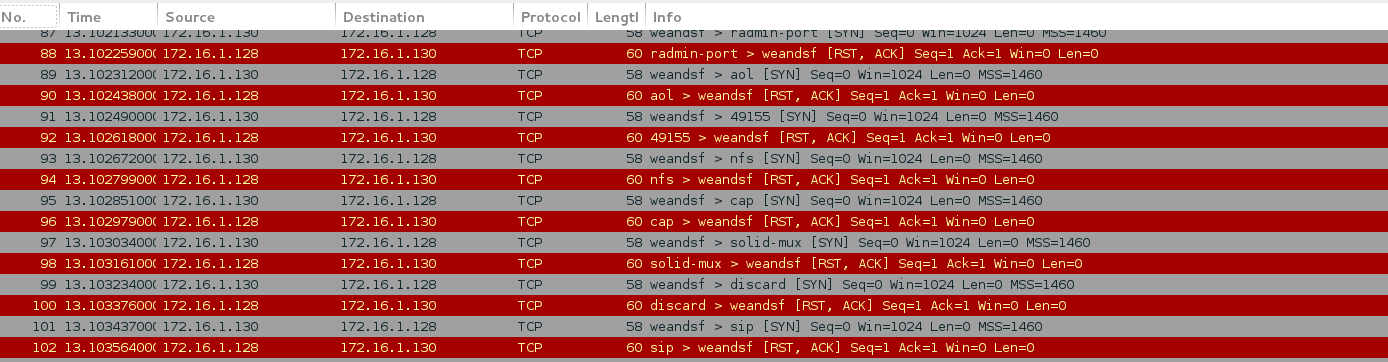
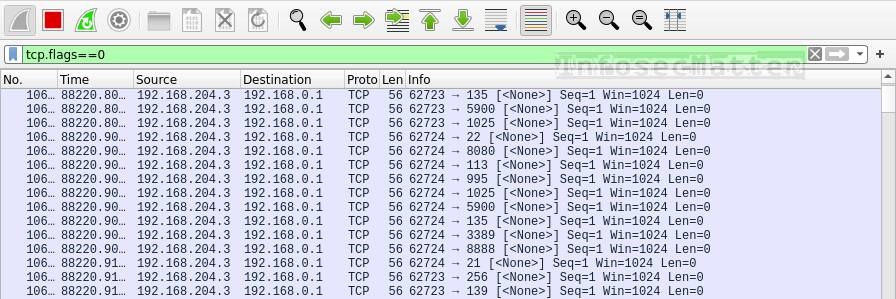
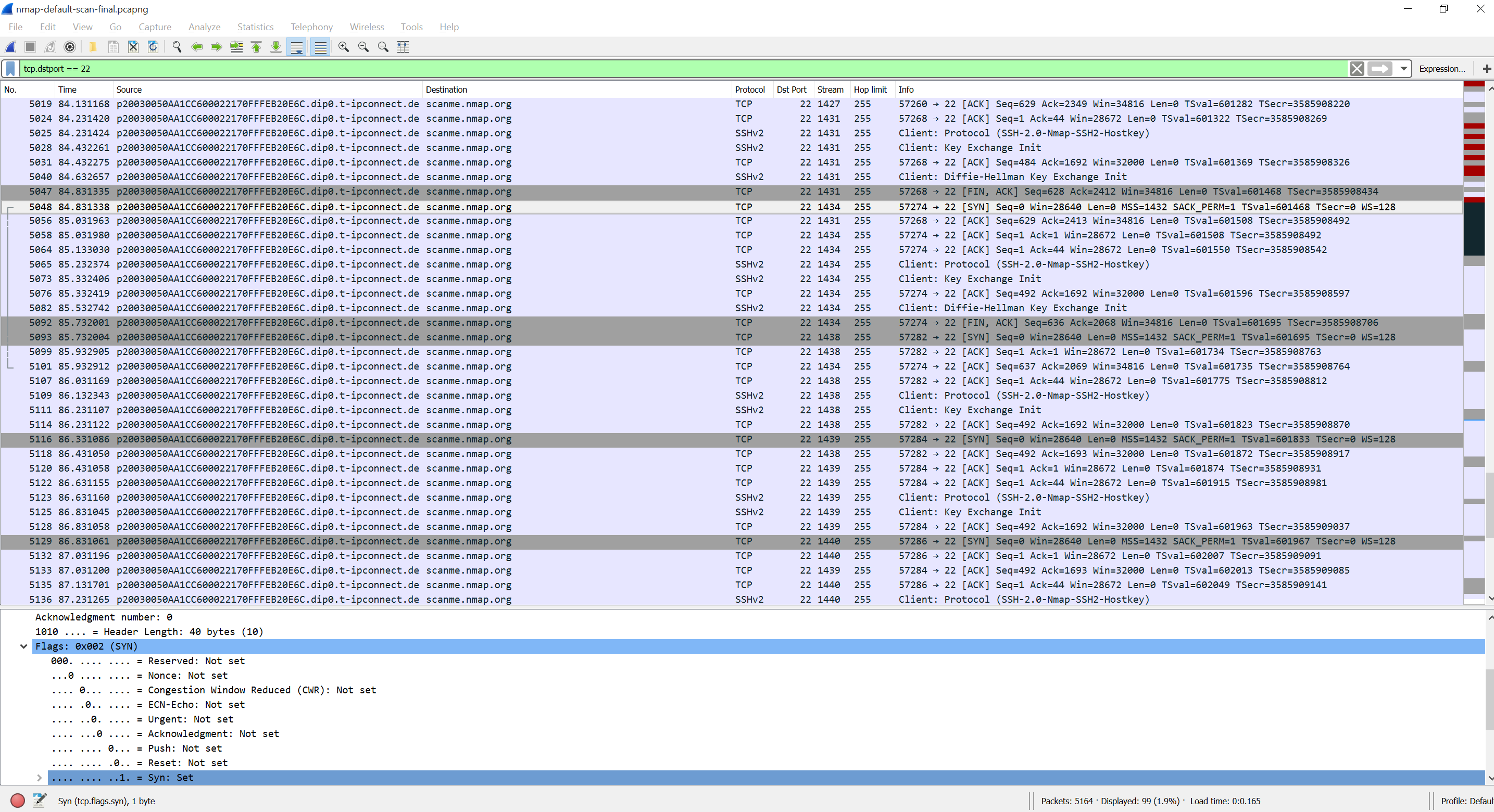
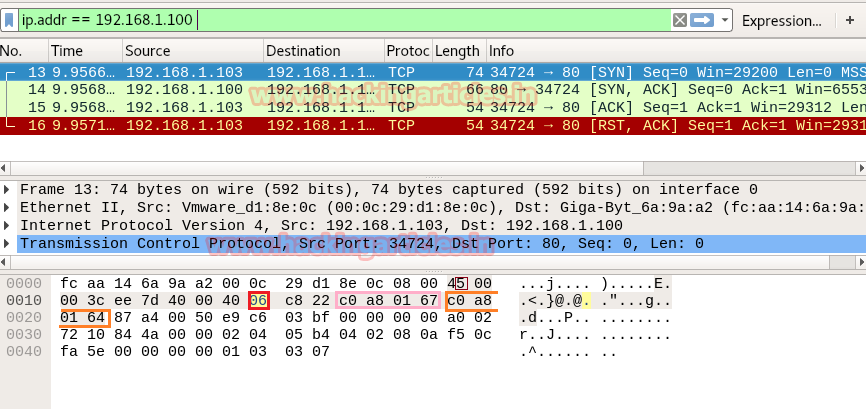
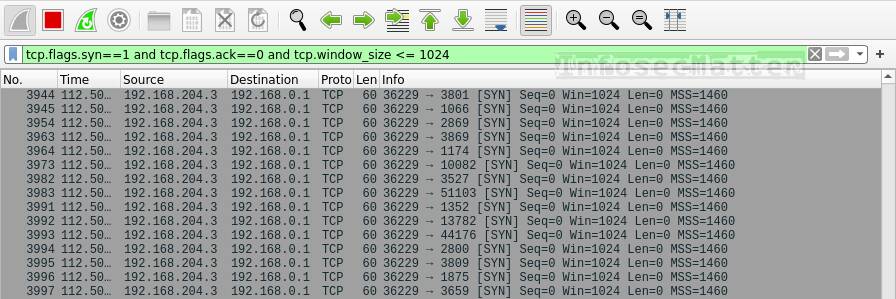
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 10 (Identifying Signatures of a Port Scan & DoS Attack) « Null Byte :: WonderHowTo
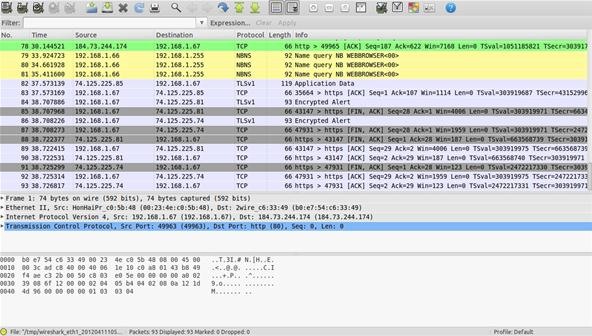
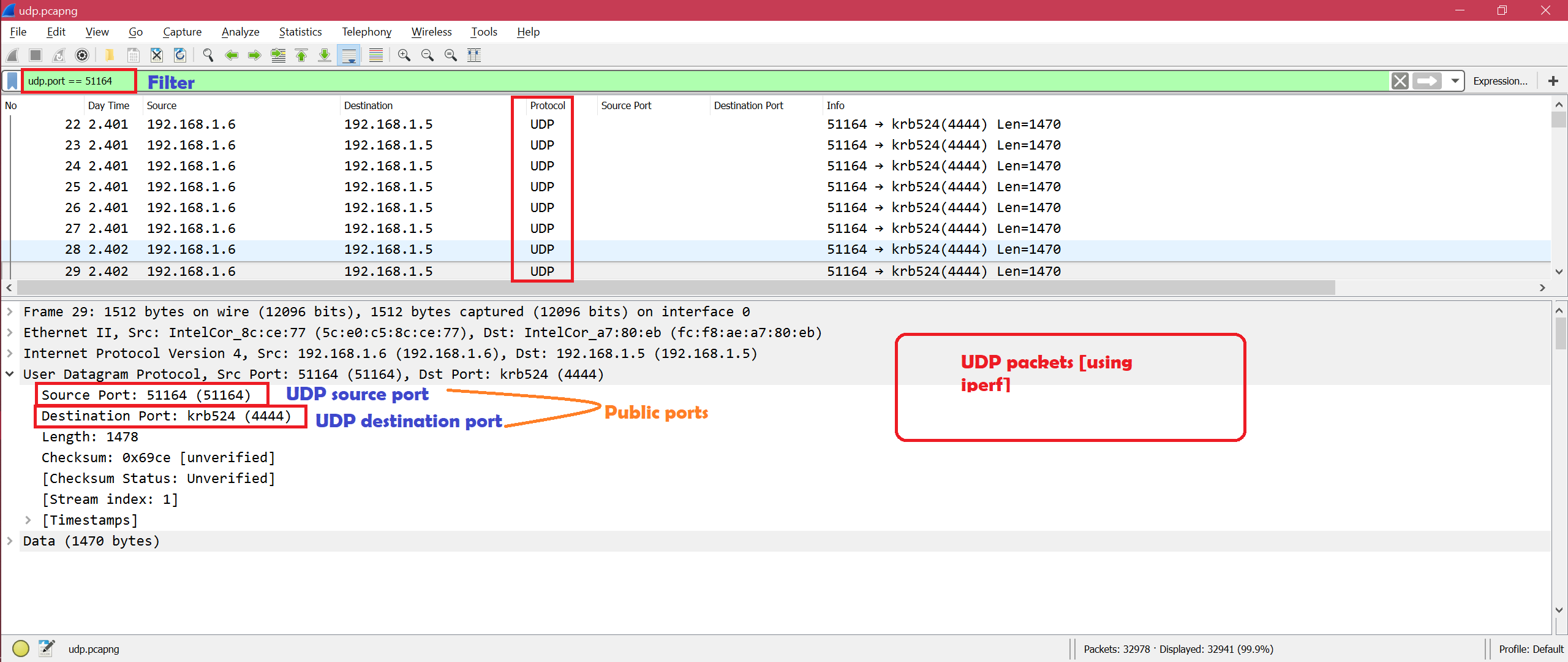
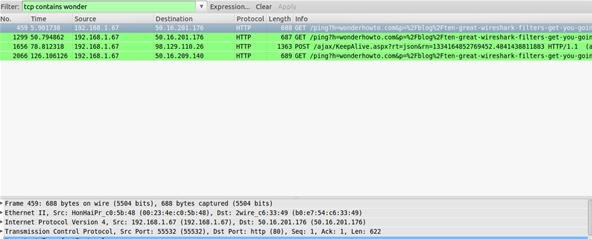
8 Wireshark Filters Every Wiretapper Uses to Spy on Web Conversations and Surfing Habits « Null Byte :: WonderHowTo