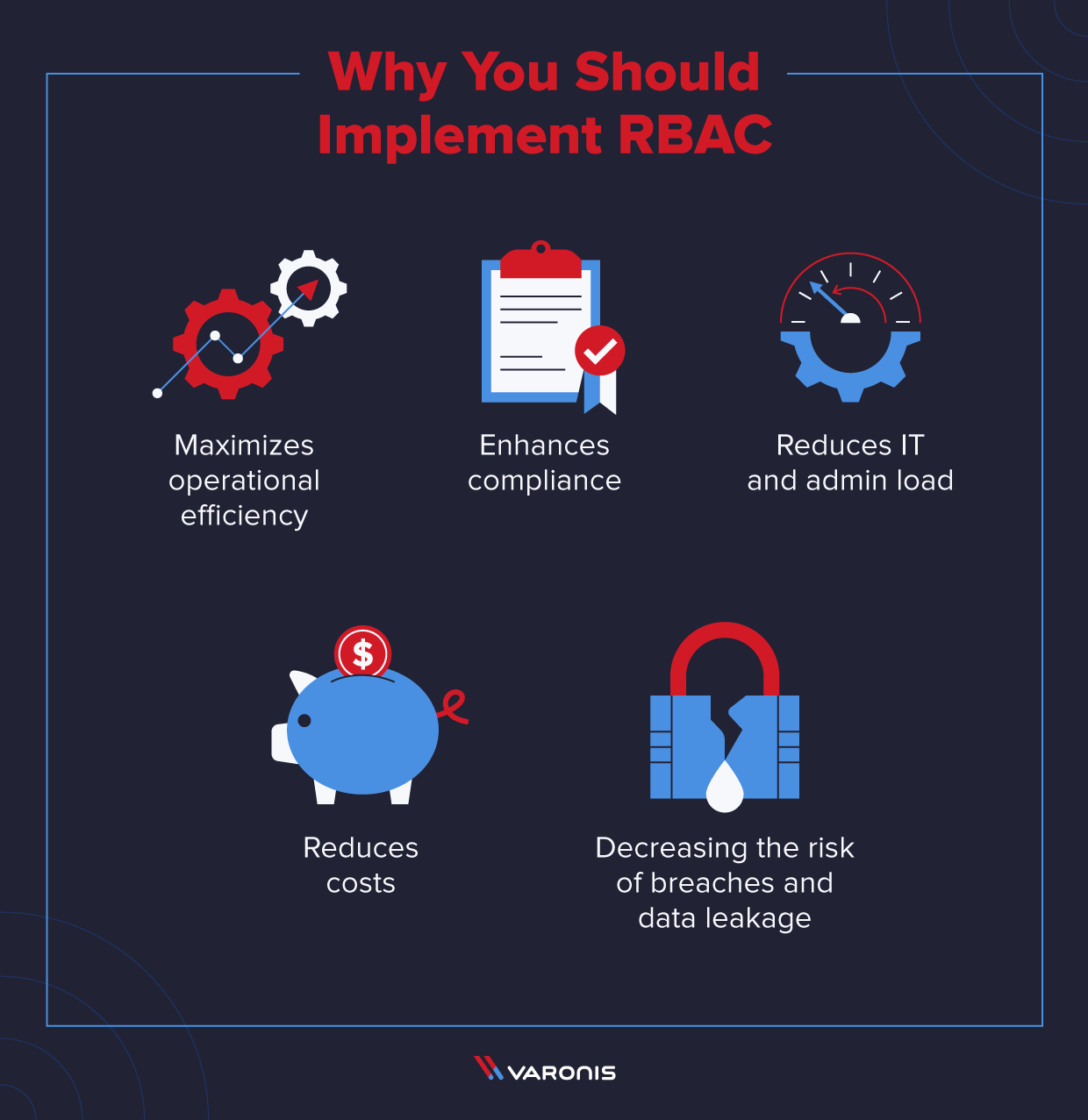
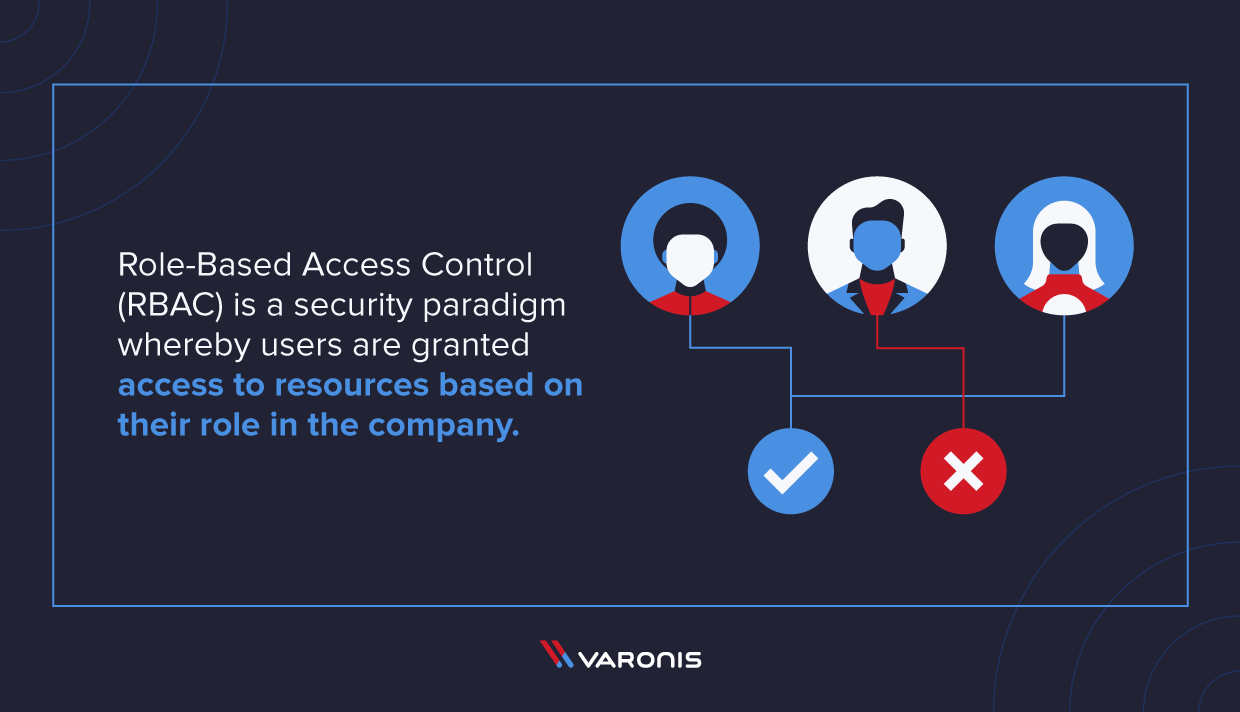
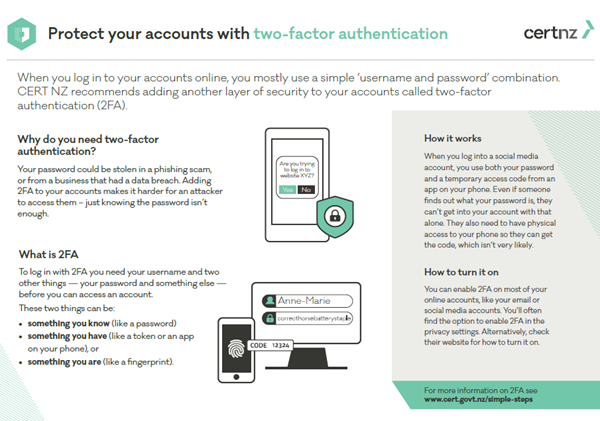
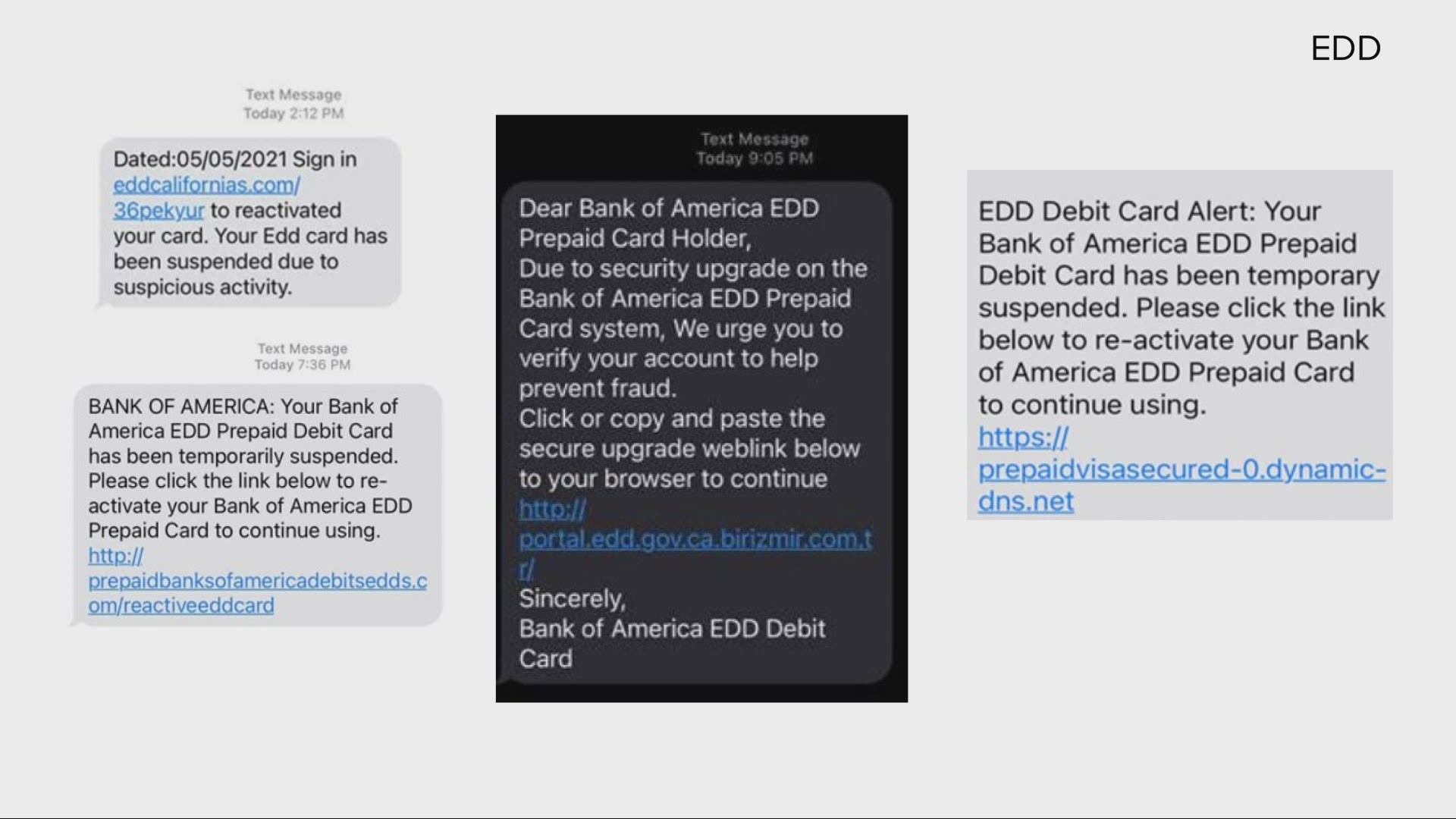
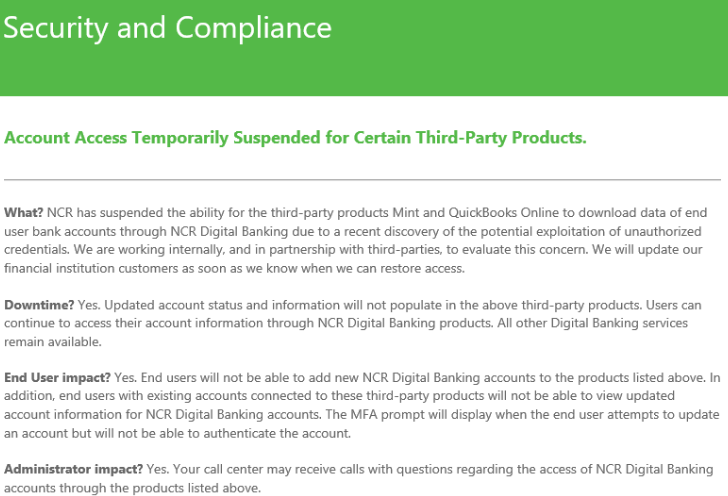
20 ways to keep your internet identity safe from hackers | Data and computer security | The Guardian
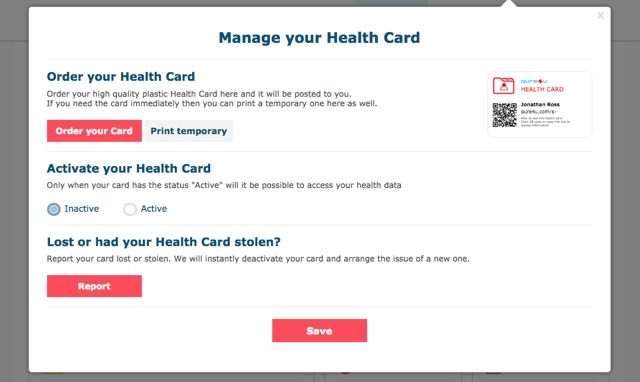
Building Privacy-Protected Data Systems Courtney Bowman Ari Gesher John Grant (of Palantir Technologies) - ppt download

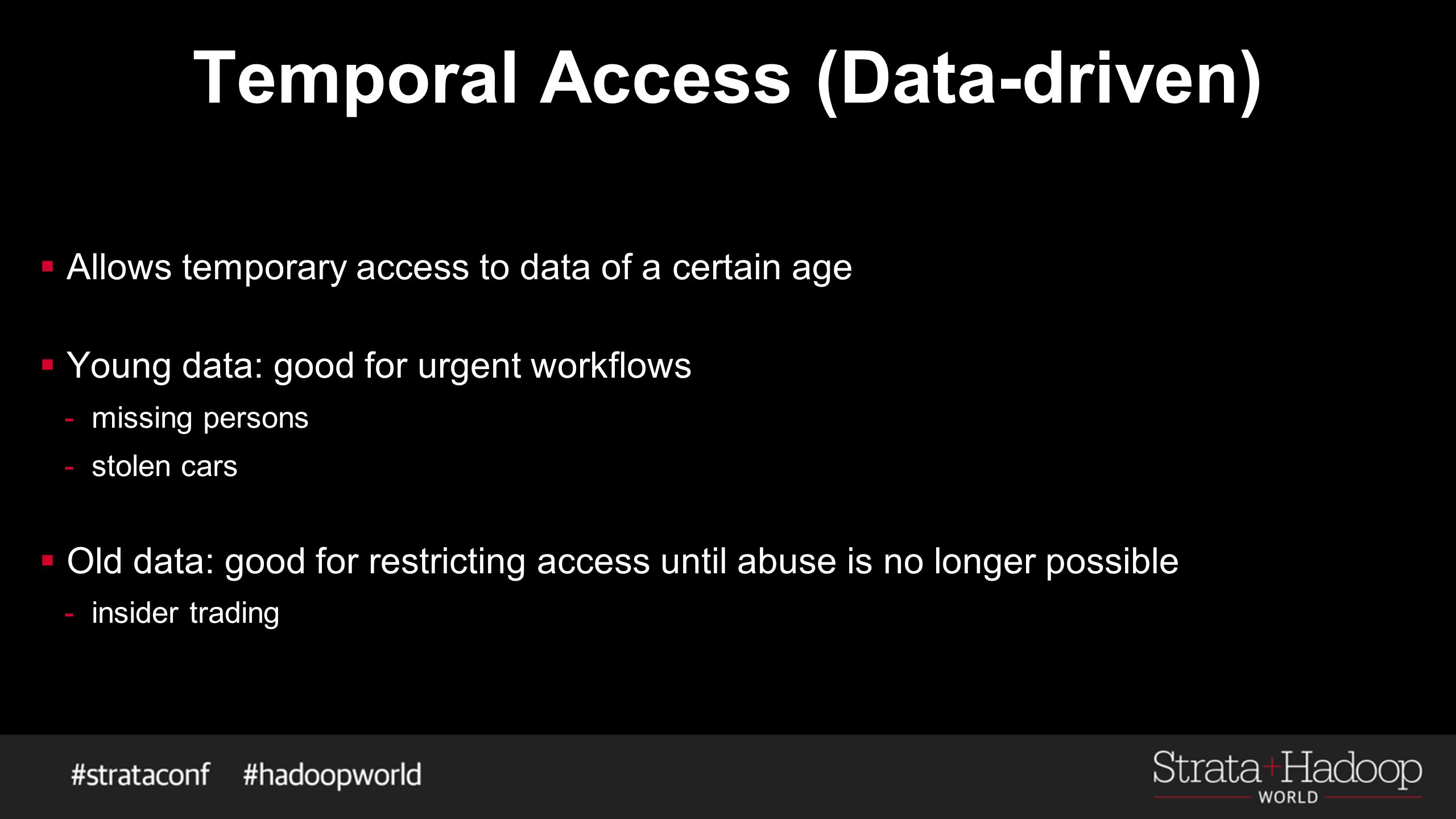
4: Outcome of breaches among those who identified any breaches in the... | Download Scientific Diagram